Bug Bounty Program

How to Participate
- Send email to: [email protected]
- Subject: [BUG] {bug title}
Rules
- Be the first one to report a specific vulnerability. Duplicate report is not eligible for bounty reward.
- Include details and verifiable proof of concept (e.g. screenshot, video, script). If our team cannot reproduce or verify the issue, then bounty cannot be awarded.
- Reporter is eligible for bounty after Rupiah Token team decide to fix the bug.
- Reporter of vulnerability is prohibited to disclose the bug to public before Rupiah Token team fixed the bug.
- Reporter of vulnerability is required to use their own account when performing testing or producing vulnerability. DO NOT attempt to view or tamper any data belonging to others.
- Reporter of vulnerability is prohibited to disturb, change, add, or delete any data or configure Rupiah Token systems, targeting other users, or compromising the reputation of Rupiah Token.
- DO NOT perform DDoS or DoS attack to Rupiah Token System.
- By sending a bug report to Rupiah Token, reporter of vulnerability agrees to give Rupiah Token the full rights to keep using that bug report for internal purposes without paying any royalty, license, or intellectual property rights.
- By participating in this program, you have agreed to comply with all applicable local and international laws.
Domain & Scope
In Scope
- www.rupiahtoken.com
- api.rupiahtoken.com
Out of Scope Issues
The following issues won’t be considered for a bounty.
- Rate limit issue
- Open Redirection (we will approve for critical case, ex: steal other user’s token)
- DoS or resource exhaustion
- Client-side issues that do not effect the latest version of common browsers (Chrome, Firefox).
- HTML injection without ability to execute malicious script.
- Self XSS, CSRF, CORS without affecting other users
- Clickjacking.
- SPF, DKIM and DMARC issues.
- Social Engineering
Severity and Reward
Reward amounts are vary depend on the severity of the vulnerability and it’s impact to Rupiah Token. We use the the international standard for risk calculations that is OWASP Risk Rating Methodology.
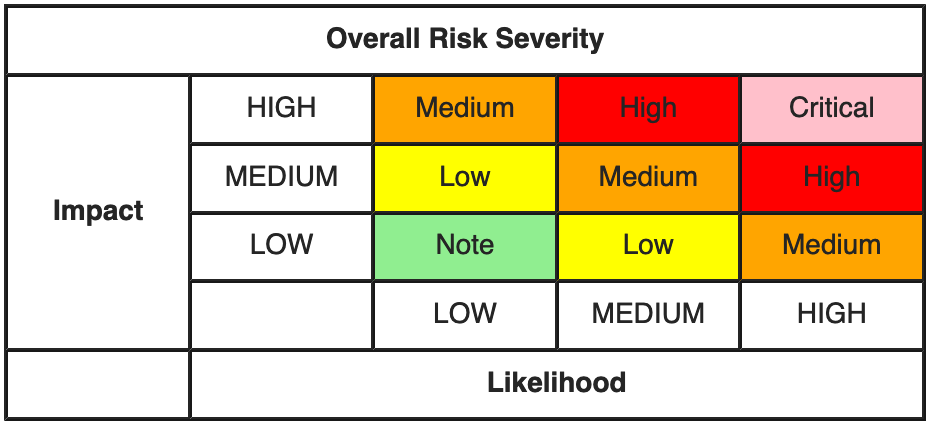
Only medium, high and critical will get reward.
What we consider?
| Likelihood Factors | Impact Factors |
|---|---|
| Skill Level | Loss of confidentiality |
| Motive | Loss of Integrity |
| Opportunity | Loss of Availability |
| Size | Loss of Accountability |
| Ease of Discovery | Financial Damage |
| Awareness | Non-compliance |
| Ease of Exploit | Reputation Damage |
| Intrusion Detection | Privacy Violation |
Reward
| Name | Reward Point | Reward IDRT |
|---|---|---|
| Low | 1 | 0 |
| Medium | 3 | 500,000 – 1,000,000 |
| High | 6 | 2,000,000 – 4,000,000 |
| Critical | 10 | 6,000,000 – 10,000,000 |
Reward will be transferred using IDRT or IDRTB.
Please make sure you have erc20 / binance chain based wallet.









